Our Service
Endpoint and application security solutions
- Web Application Firewall (WAF)
- Mobile Device Management (MDM)
- Application Security Scanning
- Valuable Data Protection
Loading
Nullam dignissim, ante scelerisque the is euismod fermentum odio sem semper the is erat, a feugiat leo urna eget eros. Duis Aenean a imperdiet risus.

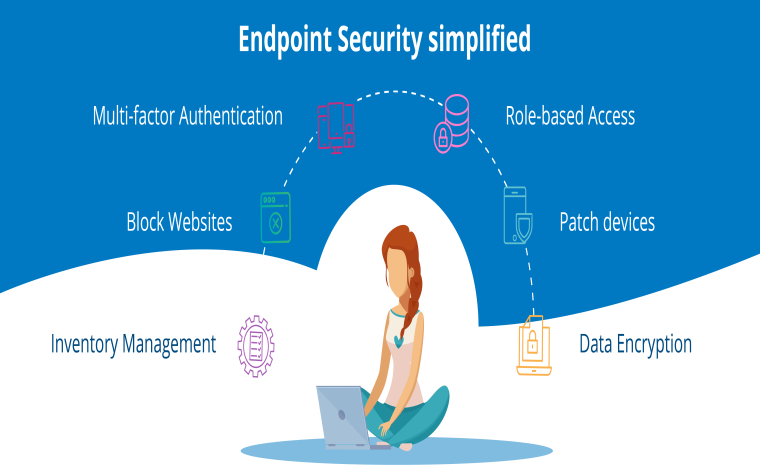
Create a data-driven culture with business intelligence for all. Reduce the added cost, complexity, and security risks of multiple solutions with an analytics platform that scales from individuals to the organization as a whole.
Our Cloud professionals present multiple solutions on their Azure hosting environment including infrastructure, virtualization, mobile apps, web application, and data warehousing.
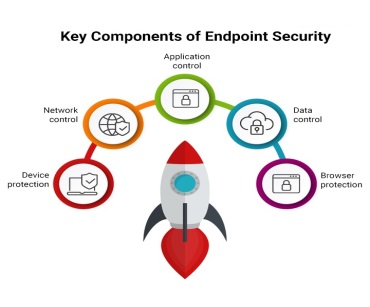
Endpoint and application security solutions
Protect your networks from an unauthorized access, misuse, modification, or disruption by implementing effective network security measures.

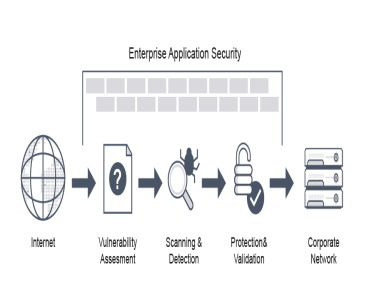
The is ipsum dolor sit amet consectetur adipiscing elit. Fusce is eleifend porta arcu In hac habitasse the platea thelorem turpoi dictumst. In lacus libero faucibus malesuada.